CYBERRANGE
The STM Cyber Range Platform has been developed to enhance the competencies of cybersecurity personnel, measure and monitor their development through practical exercises, and test the skills acquired from training in live exercise environments. Its primary objective is to comprehensively advance both theoretical knowledge and practical skills through real-world, scenario-based applications.
The Cyber Range Platform offers an integrated online solution for cybersecurity training, scenarios, labs, and exercises.
Within the platform, training content is available at basic, intermediate, and advanced levels across categories such as Introduction to Cybersecurity, Linux/Windows Operation and Security Management, Digital Forensics, Network and Web Application Security, Reverse Engineering, Cryptology, Mobile Application Security, Programming, Social Engineering, and Open Source Intelligence (OSINT).
Access and User Management
Access to the platform is provided via the internet using personal usernames and passwords. User accounts are managed through an administrator interface. The platform supports simultaneous active usage by up to 80 users.
Attack Machine
Within the platform, a Linux-based attack machine equipped with various cybersecurity tools is accessible through a web browser. A separate instance is launched for each user, featuring a default session duration of one hour, which can be extended as needed.
VPN Connectivity
Users connect to the platform and their dedicated isolated networks via OpenVPN version 3 or higher. Installation support is provided for Windows, Linux, and macOS systems.
Core Modules
- Academy Module: Provides theoretical training and fundamental skill development.
- Warm-up Module: Single-machine, step-by-step penetration testing scenarios.
- Scenario Module: More complex penetration testing scenarios involving one or multiple machines.
- Lab Module: Practical learning environments for specific tools, techniques, or vulnerabilities.
- Exercise Module: Real-time, team-based attack and defense exercises.
Core Modules and Their Functions
Academy Module
- Consists of two parts:“Pathways”, offering sequential trainings for specific areas of expertise, and“Categories”, providing topic-based, non-sequential learning options.
- Includes PDF documents, quizzes, and where necessary, hands-on lab tasks.
- Upon completion, knowledge and skills are assessed through exams featuring multiple-choice questions, text input responses, or lab completions, and users earn points based on their performance.
Warm-Up Module
- Delivers user-specific, single-machine environments featuring three-stage penetration testing scenarios:
- Single-step exploitation
- Multi-step exploitation
- Privilege escalation
- Single-step exploitation
- Each warm-up exercise comes with a solution guide provided in PDF format.
- Users are given a target IP address or domain name and earn points for correctly answering associated questions.
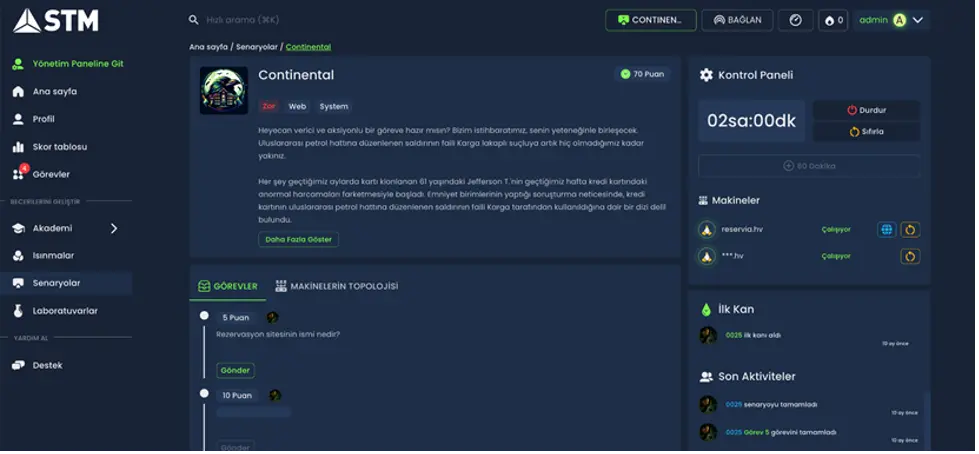
Scenario Module
- Provides custom user environments involving one or more virtual machines.
- Scenarios can be filtered and listed based on category, difficulty level, and operating system.
- Each scenario includes questions, hints, and scoring mechanisms.
- For multi-machine scenarios, network diagrams are displayed for better visualization.
- Users can rate the difficulty of scenarios they complete.
Scenario content is divided into three categories:
- Offensive (Penetration Testing)
- Defensive (Attack Analysis)
- Strategic (Combining offensive and defensive perspectives)
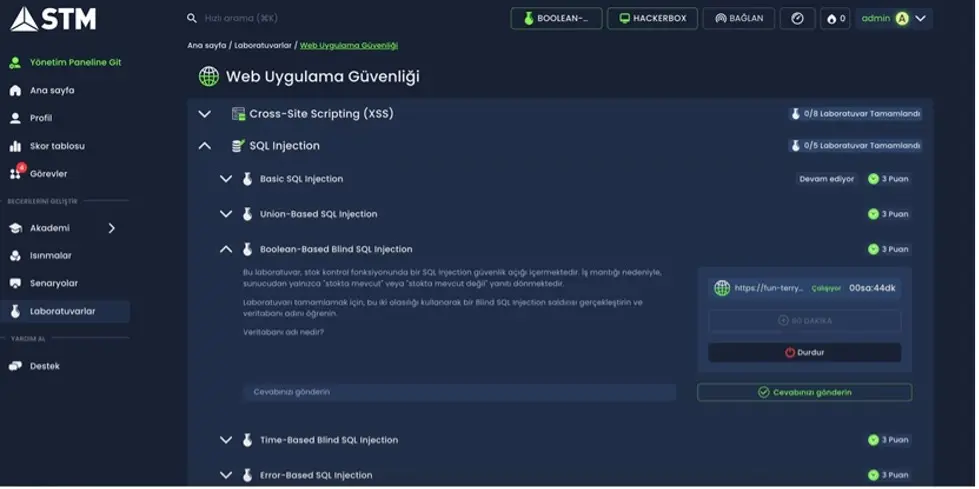
Lab Module
- Offers categorized labs designed to focus on specific vulnerabilities, techniques, or tools.
- Targets may consist of IP addresses, domain names, or files.
- Provides dedicated environments for practicing exploitation or analysis techniques.
- Completion can involve exploiting vulnerabilities, answering questions, or submitting flags, all of which contribute to point accumulation.
Exercise Module
- Designed for real-time, team-based attack and defense exercises, supporting up to 20 participants per exercise.
- General system usage instructions and information on users and teams are shared via a dedicated wiki page.
- Participants can communicate securely in a controlled environment through a chat infrastructure, allowing interaction both within their own teams and with referees, based on assigned roles and privilege levels.
- Each participant has access to inventory information related to their assigned virtual machines and resources.
- During exercises, any discovered vulnerabilities or critical findings can be submitted via structured forms within the system. Each submission is evaluated and scored based on criteria such as accuracy and criticality level.
- All findings submitted by participants are scored in real time according to pre-defined criteria and displayed on a live scoreboard visible to all teams.
- Teams can connect to their allocated systems using RDP, VNC, or SSH protocols.
Management Panel and Reporting
The Management Panel comprises three main sections:Authorization, Task Assignment, and Reporting.
- Administrators can assign users to complete specific pathways, training modules, scenarios, or labs.
- Tasks are communicated via email notifications or in-platform alerts, and each task has an associated deadline.
- Reports can be generated to show the number of trainings, scenarios, and labs completed by users daily or over specific time periods.
- Skill maps can be generated based on users’ completed activities, providing insights into their expertise levels.
- Group administrators can access detailed statistics, skill maps, and exam results for all users under their management.
Other Areas of Activity
While prioritizing Türkiye’s defense industry requirements, we diversify our technology-based operations to address the needs of both the public and private sectors, delivering innovative solutions across a broad spectrum.





